Security Light Wiring Diagram: Keep Your Home Safe and Bright! How is edge security helping secure edge ai devices?
If you are looking for How AI in Cybersecurity Reimagines Cyberthreat you've visit to the right place. We have 25 Images about How AI in Cybersecurity Reimagines Cyberthreat like Global Security Industry Powered by Need for Niche Security Solutions, Security Companies Johannesburg | Complete List 2023 and also Closed Padlock on digital background, cyber security 7812163 Vector Art. Read more:
How AI In Cybersecurity Reimagines Cyberthreat
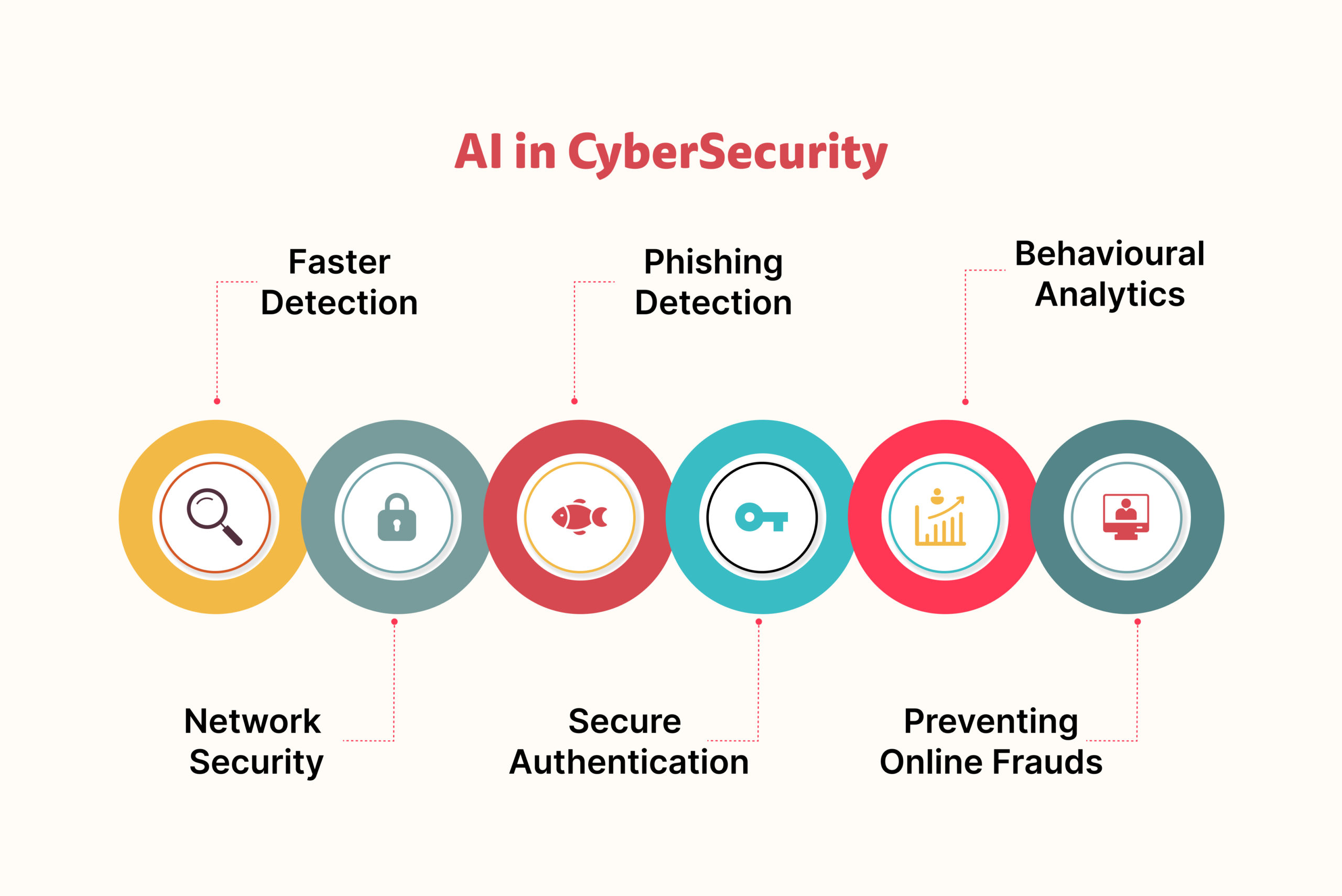 www.orangemantra.com
www.orangemantra.com
How AI in Cybersecurity Reimagines Cyberthreat
7 Best Practices Of Data Security For Businesses In Tech - Corporate
 www.corporatevision-news.com
www.corporatevision-news.com
7 Best Practices of Data Security for Businesses in Tech - Corporate ...
Closed Padlock On Digital Background, Cyber Security 7812163 Vector Art
 www.vecteezy.com
www.vecteezy.com
Closed Padlock on digital background, cyber security 7812163 Vector Art ...
There Is A New Focus On Physical Security And Cyber Security Convergence
 www.grcviewpoint.com
www.grcviewpoint.com
There Is A New Focus on Physical Security and Cyber Security Convergence
Seeking Justice For Inadequate Property Security? Learn More!
 keepaustinsafe.com
keepaustinsafe.com
Seeking Justice for Inadequate Property Security? Learn More!
Millennials Want The Security Of Their Own Roof Over Their Heads
 www.businessoutreach.in
www.businessoutreach.in
Millennials want the security of their own roof over their heads
What Is Cybersecurity? - Forage
 www.theforage.com
www.theforage.com
What Is Cybersecurity? - Forage
Understanding The 3 Phases Of Cybersecurity Architecture | Ardoq
 www.ardoq.com
www.ardoq.com
Understanding the 3 Phases of Cybersecurity Architecture | Ardoq
Global Security Industry Powered By Need For Niche Security Solutions
 www.frost.com
www.frost.com
Global Security Industry Powered by Need for Niche Security Solutions
Greater Business Security Flexibility With Alarm System Partitions - EPS
 www.epssecurity.com
www.epssecurity.com
Greater business security flexibility with alarm system partitions - EPS
What To Look For In Travel Security And Executive Protection Services
 www.securitymagazine.com
www.securitymagazine.com
What to Look for in Travel Security and Executive Protection Services ...
Innovations And Breakthroughs From Nigerian Security Scholars
 disciplines.ng
disciplines.ng
Innovations and Breakthroughs from Nigerian Security Scholars
Reviewing The 5 Stages Of The Cybersecurity Lifecycle [+ EXAMPLES]
![Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES]](https://www.cimcor.com/hs-fs/hubfs/Cybersecurity Lifecycle.jpg?width=2240&height=1260&name=Cybersecurity Lifecycle.jpg) www.cimcor.com
www.cimcor.com
Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES]
What Is Cybersecurity And Why Is It Important? - Allied Digital Blogs
 www.allieddigital.net
www.allieddigital.net
What is Cybersecurity and Why is it Important? - Allied Digital Blogs
7 Key Skills To Become A Professional Security Guard » Tell Me How - A
 www.tellmehow.co
www.tellmehow.co
7 key skills to become a professional security guard » Tell Me How - A ...
Security Considerations For Deploying Notes Plugins
 www.bcchub.com
www.bcchub.com
Security Considerations for Deploying Notes Plugins
Best Practices And Cybersecurity Tips For Remote Workers – JK Technology
 jktech.com.sg
jktech.com.sg
Best Practices And Cybersecurity Tips For Remote Workers – JK Technology
Top ICT Tenders: Consumer Commission Looks To Security | ITWeb
 www.itweb.co.za
www.itweb.co.za
Top ICT Tenders: Consumer Commission looks to security | ITWeb
The Major Concern Of Every Person Has To Be Their Security - Ivy
 ivycastellanos.com
ivycastellanos.com
The major concern of every person has to be their security - Ivy ...
Agent De Sécurité Filtrage - Www.securitsolutions.fr
 www.securitsolutions.fr
www.securitsolutions.fr
Agent de sécurité filtrage - www.securitsolutions.fr
Professional Security Services In Punjab And India | Manpower
 mpmp.in
mpmp.in
Professional Security Services in Punjab and India | Manpower ...
What Is Manned Guarding In The Security Industry
 www.kingdom.co.uk
www.kingdom.co.uk
What is manned guarding in the security industry
Security Companies Johannesburg | Complete List 2023
 www.wisemove.co.za
www.wisemove.co.za
Security Companies Johannesburg | Complete List 2023
How Is Edge Security Helping Secure Edge AI Devices?
 xailient.com
xailient.com
How is Edge Security Helping Secure Edge AI Devices?
How A Physical Security Presence Can Improve Your Cyber Security
 abbeysecurity.co.uk
abbeysecurity.co.uk
How a physical security presence can improve your cyber security ...
Security considerations for deploying notes plugins. What to look for in travel security and executive protection services. Seeking justice for inadequate property security? learn more!